Security By Design
Security by design represents a foundational approach that seamlessly integrates security measures and considerations into the very fabric of systems, products, and processes right from their inception. This proactive methodology prioritizes the early identification and mitigation of potential security risks, rather than relying solely on reactive measures after vulnerabilities have been exposed. By incorporating security as an inherent part of the design process, Matillion fosters the creation of robust and resilient systems that possess the capability to effectively withstand and deter cyber threats.
Security Whitepaper - Our Security Whitepaper also describes how we focus on maintaining customer trust through our rigorous security protocols and provide a clear understanding of our proactive approach to security, which meets or exceeds industry standards as reflected in every part of the Matillion Security Framework.



Privacy Compliance
GDPR
Matillion complies with all obligations under the European Union’s General Data Protection Regulation (GDPR) and DPA2018.
CCPA
Whilst we do not store or process much personal information of our customers, Matillion still complies with all obligations under the California Citizens Privacy Act.
HIPAA
Matillion complies with HIPAA requirements for Protected Health Information (PHI) and will sign an appropriate Business Associate Agreement (BAA) with customers who are subject to HIPAA.
Ongoing Risk Assessment
To continually enhance our security posture, Matillion performs ongoing evaluations of potential risks across all aspects of our organization, from internal operations to our diverse portfolio of products and services. We understand that the landscape of security is ever-changing and accept that no product, person, or process is ever complete, as such, we are committed to ongoing improvements and innovations while demanding quality within our security program.

Matillion Certifications and Attestations

SOC1 TYPE2
SOC1 Type 2 accreditation demonstrates the commitment from Matillion to create, implement and maintain security policies and practices that address and adhere to AICPA principles. It reports on the fairness of the presentation of management’s description of the service organization’s system and the suitability of the design and operating effectiveness of the internal controls to achieve the control objectives included in the description throughout a specified period.

SOC2 TYPE2
Matillion undergoes SOC2 external audit once a year to demonstrate the continuous monitoring of controls designing, implementation and operating effectiveness levels in accordance with the AICPA’s criteria.

SOC3 Report
SOC3 Report demonstrates the commitment from Matillion to Customers that company's security controls are trustworthy.

ISO 27001 : 2022
Matillion is now ISO 27001 : 2022 compliant. Matillion maintains an Information Security Management System (ISMS) that aligns with the requirements of the ISO/IEC 27001:2022 standard. This certification demonstrates that Matillion has a structured and proactive approach to managing and protecting sensitive information.

PCI DSS 4.0.1
Matillion is now PCI DSS 4.0.1 certified, providing an extra layer of security and assurance for businesses handling payment card data. Our PCI DSS certification demonstrates Matillion's commitment to the highest security standards, ensuring your data pipelines are protected with robust compliance controls. With Matillion DPC's new PCI DSS compliance, you can confidently build data pipelines, knowing your data security meets the stringent requirements of the payment card industry.

CSA Star
Matillion have completed the Consensus Assessments Initiative Questionnaire (CAIQ) to document compliance with the Cloud Controls Matrix (CCM). This is a transparent document providing customer visibility into specific provider security practices.
Documents
Matillion Quality in Test Strategy
PCI DSS 4.0.1 AOC
SOC2 TYPE2 Report 2024-2025
AI Security Whitepaper
DPC Penetration Executive Summary
SOC3 Report
SOC1 TYPE2 Bridge Letter
ISO 27001 : 2022 Certificate
SOC1 TYPE2 Report
Matillion GxP Guidelines
Security Whitepaper
Network Diagram




Trust Center Updates
Conclusion of our Salesloft Drift Security Breach Investigation
IncidentsWe have now completed our investigation into the recent Salesloft Drift security incident, which resulted in limited data exposure within Matillion’s Salesforce tenant.
While our investigation is now concluded, our teams continue to take additional steps to further strengthen our security environment.
As a precaution, we encourage you to remain alert to potential targeted phishing attempts that may arise from this incident.
If you have any questions or need further support, please contact us at [email protected].
Thank you for your continued trust.
Published at 19-09-2025 19:07:00
Salesloft Drift Security Breach: What We Know So Far and How We’re Responding
IncidentsAt Matillion, integrity and customer trust guide everything we do. We believe in transparency and safeguarding the data that powers your business.
What Happened?
We want to make you aware of a recent social engineering campaign aimed at Salesforce customers.
As part of this activity, attackers have been able to compromise OAuth tokens from within the third-party application Salesloft Drift. Like many organisations, Matillion uses Salesloft Drift, which is a chat application that integrates with Salesforce and powers website’s chatbots to guide visitors, support customers, connect prospects with our sales team and automate sales workflows. This attack is similar to other Salesforce-related incidents reported across multiple organizations in recent weeks.
We were recently informed that Matillion credentials used to integrate Salesloft Drift with Salesforce were compromised, which may have allowed the attackers to view a portion of our data in Salesforce. Our investigation confirms that this access was very limited and the incident was contained to data stored in Salesforce only. No other Matillion environments or systems were affected.
This in no way affects customer data in Data Productivity Cloud (DPC), Maia or Matillion ETL (METL). Pipeline and authentication remains secure due to our data isolation architecture.
What information was impacted?
We have reviewed all queries executed against our Salesforce tenant by the threat actor and continue to work with Salesforce to obtain further detailed logs and support our ongoing investigation. However, out of abundance of caution and in line with our belief in transparency, we are notifying customers as your data may have been compromised.
Due to the way that the queries were executed in Salesforce we cannot provide the exact data that has been exfiltrated as Salesforce does not log SOQL responses, however we have determined that the following data types were included:
- Contact Information: Names, Business Email Addresses, Phone Numbers, Business Location, LinkedIn Profile URL’s
- Support Case Data: Subject, Description
- Commercially Sensitive data: Feature Requests made by customers and Matillion’s Roadmap Details
- Technical System data: Matillion Hub Login IP addresses, Matillion Hub Role Name
- Authentication for DPC and Hub is a separate system and database with no path between it and Salesforce. This data has not been impacted.
- Financial and Billing data: Contract Values, Partial Credit Card Numbers.
- Payment data is stored in accordance with PCI-DSS by our payment provider Recurly. The Recurly platform was not directly impacted by this, only related data that was stored in Salesforce.
In further response to a related Google Threat Intelligence report on these attacks, we scanned all support case data to identify credentials, secrets or access keys that may have been unintentionally included in support tickets raised to us. In the exceptionally few cases where such information was found, we have proactively reached out to the affected customers to ensure appropriate containment and investigation steps have been taken.
What have we done?
Our security team has taken the following steps after being notified of the incident:
- Contained the compromise by ensuring the Salesloft Drift application no longer has access to our Salesforce tenant
- Reviewed the data included in the unauthorised queries executed against our Salesforce tenant
- Determined what sensitive information could potentially be impacted
- Contacted customers to rotate credentials, secret or access keys which were unintentionally included in support tickets raised to us
If you have not already been contacted by us regarding rotating credentials, we have not identified any affected credentials related to your resources.
What can our customers do?
The impacted information could be used for targeted phishing attacks and we therefore advise vigilance when being contacted.
Please note, Matillion will never ask you for sensitive information like credentials. If you are in doubt of a communication from Matillion, please reach out to your account team directly or contact [email protected].
We want to assure you that the security of your data is our highest priority. We will share more information as it becomes available.
References
Salesloft Drift Security Incident Disclosure
Published at 29-08-2025 29:57:00
Phishing Attempt Targeting BACS Details
GeneralWe recently became aware of a phishing attempt targeting one of our customers. The malicious communication attempted to trick the recipient into updating the payment details they hold for us.
We urge all our customers to remain vigilant against such fraudulent activities. Please be aware of the following:
- Matillion will never ask you to change our bank details via email. Any legitimate changes to our banking information would be communicated through official, verified channels, typically involving direct contact.
- Always verify suspicious requests. If you receive an email or communication requesting a change to payment details or other sensitive information, even if it appears to be from Matillion, do not act on it immediately. Instead, verify the request through a separate, trusted communication channel (e.g., calling your known Matillion contact directly). Do not use contact information provided in the suspicious email.
- Look out for common phishing indicators. These can include urgent or threatening language, unsolicited attachments or links, misspellings or poor grammar, and sender addresses that appear similar but are not exactly correct.
If you suspect you have received a phishing email, please report it to us immediately at [email protected] and refrain from clicking on any links or downloading any attachments.
Published at 28-07-2025 28:28:00
CVE-2024- 52316 - Authorisation Bypass Vulnerability in Jakarta
VulnerabilitiesMatillion is aware of a recent security vulnerability identified in versions of Jakarta
- Tomcat versions 11.0.0-M1 through 11.0.0-M26
- Tomcat versions 10.1.0-M1 through 10.1.30
- Tomcat versions 9.0.0-M1 through 9.0.95
Matillion Data Productivity Cloud
Matillion Data Productivity Cloud is not affected by this vulnerability.
Matillion ETL
Matillion ETL does not use Jakarta by default and therefore is not affected by this vulnerability
References
https://www.recordedfuture.com/vulnerability-database/CVE-2024-52316
Published at 11-04-2025 11:56:00
"IngressNightmare" - RCE Vulnerability in Nginx Admission Controller
VulnerabilitiesMatillion is aware of recent security vulnerabilities identified in versions of Nginx Admission Controller which is a component of the Nginx Ingress Controller for Kubernetes (CVE-2025-1097, CVE-2025-1098, CVE-2025-24514 and CVE-2025-1974).
- Versions before 1.12.1
- Versions before 1.11.5
Matillion Data Productivity Cloud
Matillion Data Productivity Cloud is not affected by this vulnerability.
Matillion ETL
Matillion ETL is not affected by this vulnerability.
References
https://www.wiz.io/blog/ingress-nginx-kubernetes-vulnerabilities
Published at 25-03-2025 25:00:00
CVE-2025-29927 - Authorisation Bypass Vulnerability in Next.js
VulnerabilitiesMatillion is aware of a recent security vulnerability identified in versions of Next.js.
- Next.js 15.x versions before 15.2.3
- Next.js 14.x versions before 14.2.25
- Next.js 13.x versions before 13.5.9
Matillion Data Productivity Cloud
Matillion Data Productivity Cloud is not affected by this vulnerability.
Matillion ETL
Matillion ETL is not affected by this vulnerability.
References
https://snyk.io/blog/cve-2025-29927-authorization-bypass-in-next-js-middleware/
Published at 25-03-2025 25:51:00
CVE-2025-24813 - RCE Vulnerability in Apache Tomcat
VulnerabilitiesMatillion is aware of a recent security vulnerability identified in versions of Apache Tomcat.
- Tomcat 11.0.0-M1 to 11.0.2
- Tomcat 10.1.0-M1 to 10.1.34
- Tomcat 9.0.0.M1 to 9.0.98
Matillion Data Productivity Cloud
Matillion Data Productivity Cloud is not affected by this vulnerability.
Matillion ETL
Currently supported versions of Matillion ETL (1.72 (LTS), 1.75 (LTS) and 1.77 (STS)) are shipped with a version of Apache Tomcat that is reported as being vulnerable to CVE-2025-24813.
Following investigation, Matillion can confirm that the configuration of Apache Tomcat supplied with Matillion ETL prevents the exploitation of this vulnerability and as such currently supported versions of Matillion ETL are not considered vulnerable.
Apache Tomcat will be upgraded in future releases of Matillion ETL.
References
https://lists.apache.org/thread/j5fkjv2k477os90nczf2v9l61fb0kkgq
Published at 19-03-2025 19:00:00
CVE-2024-56337 - RCE Vulnerability in Apache Tomcat
VulnerabilitiesMatillion is aware of a recent security vulnerability discovered within some versions of Apache Tomcat:
- Tomcat 11.0.0-M1 to 11.0.1
- Tomcat 10.1.0-M1 to 10.1.33
- Tomcat 9.0.0.M1 to 9.0.97
Matillion Data Productivity Cloud
Matillion Data Productivity Cloud is not affected by this vulnerability.
Matillion ETL
Currently supported versions of Matillion ETL (1.72 (LTS), 1.75 (LTS) and 1.77 (STS) ) are supplied with a version of Apache Tomcat that is not vulnerable ‘out of the box’ due to the default configuration of the Java 17 system property ‘sun.io.useCanonCaches’.
If you wish to check the version of Apache Tomcat installed on your Matillion ETL instance:
- Login to Matillion ETL
- Select the ‘Help’ dropdown and click ‘Support Information’.
- Scrolling down, find the ‘Tomcat: Version’ item to see the current version of Apache Tomcat installed.
Mitigation for this particular vulnerability can be achieved through the configuration of the system property ‘sun.io.useCanonCaches’ which must be set to ‘false’. By default this value is set to ‘false’ in Java 17 and as such Matillion does not consider currently supported versions of METL to be vulnerable to CVE-2024-56337.
If you wish to check that this value is set as ‘false’ on your Matillion ETL instance, please follow these steps
- SSH to your Matillion ETL instance.
- Run the following command (‘touch useCanonCaches.java’)
- Using your preferred text editor, open the useCanonCaches.java file and add the following contents:
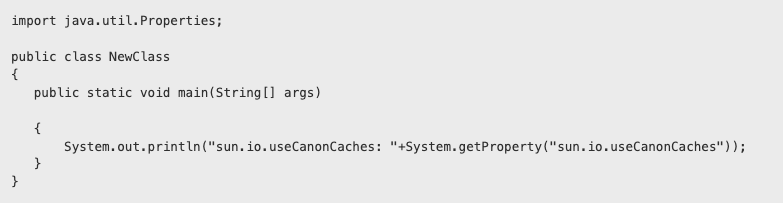
- Exit the text editor.
- Run the following command (‘java useCanonCaches.java)
- The output will confirm the set value of the sun.io.useCanonCaches property, a result of ‘NULL’ or ‘false’ confirms that this vulnerability is mitigated.
- If you receive any other value, please raise a support case for assistance.
Apache Tomcat will be upgraded in future releases of Matillion ETL as expected.
References
Published at 09-01-2025 9:00:00
CVE-2024-6387 - Vulnerability in OpenSSH - aka. regreSSHion
VulnerabilitiesUpdated 09/07/2024 10:00 GMT
Matillion is aware that a security vulnerability in a well used third party library (OpenSSH Server) was reported on the 1st July 2024 known as CVE-2024-6387 or ‘regreSSHion’.
Matillion ETL:
- All customers, regardless of version or installation method, are strongly advised to avoid facilitating internet access to their instance via SSH as per the Matillion ETL Best Practices (https://docs.matillion.com/metl/docs/matillion-etl-security-best-practices/).
- Customers who are running a Matillion ETL 1.75 AMI are running a vulnerable version of OpenSSH. To install the patch:
- Access the Matillion ETL instance command line
- Run the following command 'sudo yum update openssh'
- Once the update has completed, confirm the release installed by running the command 'sudo yum info openssh' (Case Sensitive)
- If the patch has been successfully installed, the 'Release' should show as '42.el9' rather than '41.el9'.
Note: Although the patched OpenSSH version still show as OpenSSH 8.7p1, the release 42 includes the patch for CVE-2024-6387 as mentioned in the linked changelog (https://gitlab.com/redhat/centos-stream/rpms/openssh/-/merge_requests/78/diffs).
- Customers who are running Matillion ETL 1.74 AMI and older are not running a vulnerable version of OpenSSH.
- Customers who have installed Matillion ETL using the Universal Installer are advised to check the installed version of OpenSSH on their instance using the following steps:
- Access the Matillion ETL instance command line
- Run the following command ‘ssh -V’ (Case Sensitive)
- The version of OpenSSH will be displayed. Vulnerable versions are 8.5p1 <= OpenSSH < 9.8p1 OR versions below and including 4.4p1.
- Customers running a vulnerable version should consult their Operating System vendor for advice on patching.
Matillion Data Productivity Cloud:
Data Productivity Cloud is not affected by this vulnerability.
Published at 03-07-2024 3:00:00
Remote Code Execution vulnerability in Git (CVE-2024-32002)
VulnerabilitiesRemote Code Execution vulnerability in Git (CVE-2024-32002)
Matillion is aware of the details of a critical vulnerability (CVE-2024-32002) that affects Git. We can confirm that neither Matillion ETL or Matillion Data Productivity Cloud are impacted by this vulnerability and customers do not need to take any action.
Published at 05/23/2024, 11:09 AM*
Published at 23-05-2024 23:00:00
Command Injection Vulnerability in Palo Alto PAN-OS (CVE-2024-3400)
VulnerabilitiesMatillion is aware of CVE-2024-3400 which is present in specific versions of Palo Alto PAN-OS software. We can confirm that Matillion is not impacted by this vulnerability.
Published at 04/18/2024, 3:51 PM*
Published at 18-04-2024 18:00:00
Redhat CVE-2024-3094 Discovered March 28
Matillion are aware of the Redhat CVE-2024-3094 incident discovered on March 28 (https://www.redhat.com/en/blog/urgent-security-alert-fedora-41-and-rawhide-users). This incident affects base operating system components.
That said, the current default Matillion ETL base image is Centos Stream 8 (Centos 7, prior to 1.68.) and as such, per Redhat's CVE notes, this version is not affected. You can confirm this yourself by running the xz --version command in a Bash component or terminal; it will respond with a version prior to 5.6.0: $ xz --version xz (XZ Utils) 5.2.5 liblzma 5.2.5
For customers who have installed on another base operating system than our default, or have manually forced an upgrade to this package, they should check whether they have an affected version of this library immediately. The affected versions are 5.6.0 and 5.6.1. Any systems with these versions should be stopped immediately. The exploit appears to allow root access to an attacker via SSH connection and any system which may be so contacted must be assumed to be compromised.
Published at 04/05/2024, 10:34 AM*
Published at 05-04-2024 5:30:00
(Non Security) Critical Advisory - METL Update Required
General(Non Security) Critical Advisory: Has your Matillion ETL (METL) instance stopped responding and are you unable to log in? Due to Matillion ETL (METL) license management defect, you need to patch to restore functionality. Simple to follow remediation instructions can be found here: https://docs.matillion.com/metl/docs/critical-advisory-licence-management-defect/
Published at 02/23/2024, 10:05 AM*
Published at 23-02-2024 23:00:00
libwebp image framework (CVE-2023-4863)
VulnerabilitiesMatillion's security team is aware of and responding to the announcement of a critical vulnerability in the libwebp image framework (CVE-2023-4863).
We are prioritising the rollout of security patches and the implementation of appropriate mitigation strategies to reduce the risk to our internal applications and environments.
Matillion ETL: We can confirm that the vulnerable libwebp package is present in our Matillion ETL AMI, however it is not utilised by Matillion ETL and as such we assess the risk to be low. We would recommend customers to apply the patch as soon as it is available from the vendor(s). Example: https://access.redhat.com/errata/RHSA-2023:5309
Data Productivity Cloud: Data Productivity Cloud does not to have libwebp package and as such is not considered vulnerable.
Please reach out to support if you require any assistance
Published at 09/29/2023, 8:48 AM*
Published at 29-09-2023 29:30:00
MOVEit Transfer and MOVEit Cloud Vulnerabilities
VulnerabilitiesOn May 31 and June 9, 2023, Progress Software announced the discovery of two critical vulnerabilities (CVE-2023-34362 and CVE-2023-35036) that could lead to escalated privileges and unauthorized access to their MOVEit file transfer product and environment.
On June 16, an additional critical vulnerability related to this issue, CVE-2023-35708, was announced.
Following our vulnerability response process, including a review of all environments, Matillion does not use MOVEit Transfer and MOVEit Cloud products and has no evidence at this time of any impact to customer data due to these vulnerabilities.
Published at 19-07-2023 19:00:00
User Awareness, Fraudulent site in Matillion's name.
General---Matillion has been made aware of similar domains that claim to be operated by Matillion, these include matillion-okta.com and matillion-pro.com.
Abuse claims have been raised and as of today, all sites are now down. We will continue to keep our customers updated incase of any new developments.
Kind Regards,
Published at 04/20/2023, 3:58 AM
---Matillion has been made aware of a recent fraudulent website (http://uk-matillion.com) that claims to be running a promotional program in an attempt to get victims to deposit money through the site.
Matillion is working to ensure that this site is taken down, however it felt important to make all customers aware of the situation.
Kind Regards,
Published at 04/12/2023, 12:11 PM*
Published at 20-04-2023 20:00:00
Matillion's Response to the 2022 OpenSSL 3 Vulnerabilities
IncidentsMatillion is aware of the current discussions around the OpenSSL 3.0.7 vulnerabilities. At present we do not use the library within our default images and therefore Matillion products and services are not exposed to this vulnerability. We have also found no instances of the vulnerable version within our estate but we are continuing to investigate and gain assurance. Should we determine any exposure, then the remediation of this vulnerability will be completed in line with our Vulnerability & Patch Management process. We are also assessing if there has been any exposure within our third party supply chain, but so far have found no impacted services.
Published at 11/03/2022, 9:09 AM*
Published at 03-11-2022 3:00:00
Welcome to the Matillion Security Trust Center
GeneralAs an organisation that is security conscious and values security, we are excited to announce the official launch of the Matillion Security Trust Center. By using this portal, you can request access to our compliance documents, review our standardized questionnaires such as the SIG and gain a general understanding of our security posture.
Over time, our team will be making changes to this portal as we implement new tools and processes in our environment. You can use the Subscribe button to receive email notifications for when our team has an important update, such as if we have an updated compliance report or if we have a status update regarding a major security vulnerability that has been recently discovered.
The Matillion Security Team
Published at 06/30/2022, 12:59 AM
Published at 30-06-2022 30:00:00